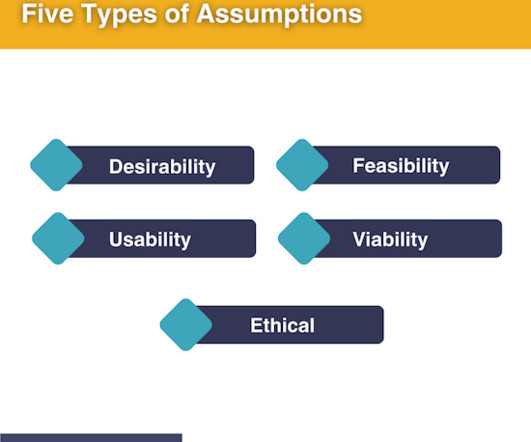
Evaluating Solutions: The 5 Types of Assumptions that Underlie Our Ideas
Product Talk
OCTOBER 11, 2023
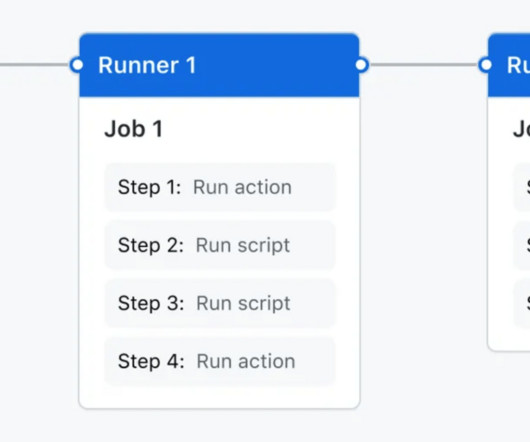
We’ve chosen this as our target opportunity and have generated three potential solutions: Add social media share buttons that allow people to quickly share the title and URL of the article. Each of these solutions depend on a number of assumptions that need to be true in order for each solution to succeed.










































Let's personalize your content