Technical Review: A Trusted Look Under the Hood
TechEmpower - Product Management
AUGUST 21, 2023
Many CEOs of software-enabled businesses call us with a similar concern: Are we getting the right results from our software team? Most innovators don’t have a technical background, so it’s hard to evaluate the truth of the situation. And unless they have a tech background, they can’t look under the hood themselves.
.jpg)




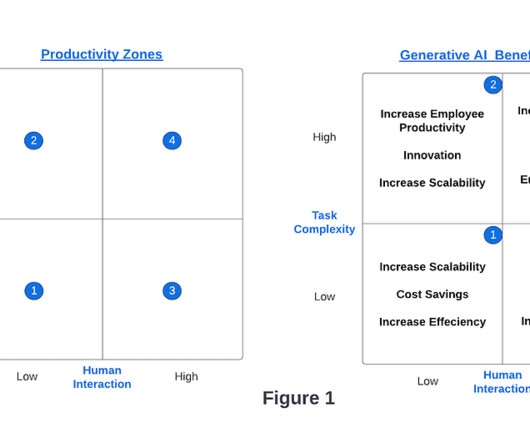













Let's personalize your content