Introducing Nulab Pass: Enterprise-grade security for all Nulab services
Nulab
AUGUST 4, 2020
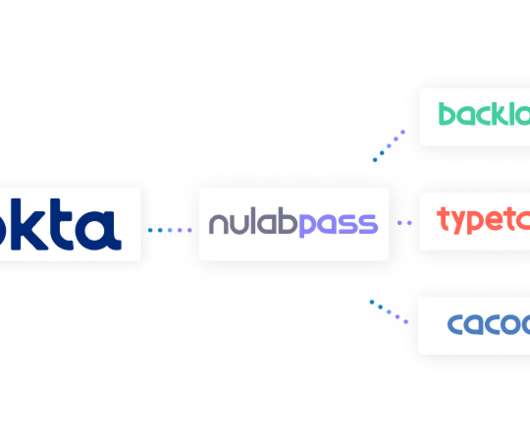
It’s our new enterprise-grade security option that we’re calling Nulab Pass. It’s our new centralized security subscription that gives you enterprise-grade security and governance of all of your Nulab apps for your entire organization. It works across all of our products, including Backlog , Cacoo , and Typetalk.







Let's personalize your content