Online Biometric Screening?—?Security Assistant For Online Businesses
The Product Coalition
DECEMBER 3, 2021
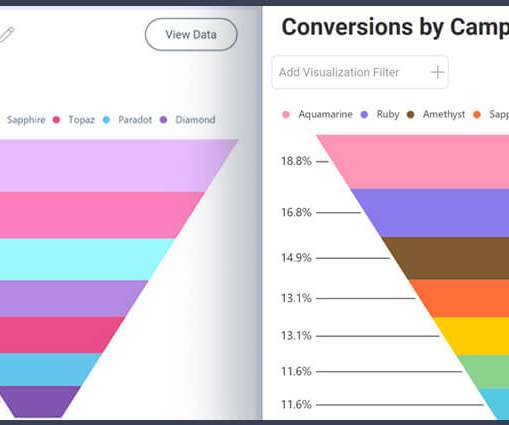
Biometrics are widely used to control access to physical and digital resources such as buildings, rooms, and computer peripherals. If the attacker sends confidential information to an intermediate file, he can hide other companies and copy the data. If the two biometric data formats match, you need to confirm.






































Let's personalize your content